In recent times, digital signatures have become vital tools in cybersecurity. They help keep us safe by identifying and protecting against online threats. But, on the flip side, threat actors can also use these signatures to target lots of devices and web applications on the internet, with the help of ip crawling websites like Censys and Shodan. This means those defending against cyberattacks need to stay alert and adjust their security measures.
Even in the world of cars, digital signatures matter. If a threat actor gets their hands on a car’s signature, they could mess with the dashboard. This is especially true for smart cars that use third-party apps for functions such as data management and control. But it’s essential to set up these apps correctly, or else hackers might get in and take control. In this blog post, we’ll talk about TeslaMate and why this matters in our digital age.
At first lets find the signature of teslamate using open source information.
1.When conducting a Google image search for “teslamate configure,” one can find information indicating that TeslaMate utilizes a Grafana instance.

2.Continuing the image search, an image of a TeslaMate instance is visible, displaying keywords “Dashboards” and “Geo-Fences.”

3.Now lets try to search through censys using query –
“TESLAMATE” and “Geo-Fences” and “Dashboard”

4.It’s giving about 1589 results, and upon opening any one of the instances, it provides information with -.

5.This teslamate instance has been configured correctly .Now what if the user has not configured the teslamate instance correctly ,is it possible to get that instances by creating a new signatures ? lets try to find that out using a new censys query –
“TESLAMATE” and “Geo-Fences” and “Dashboards” and not “sign_in”

6.Here the total number of results are 1411 ,now opening any instance is giving information –
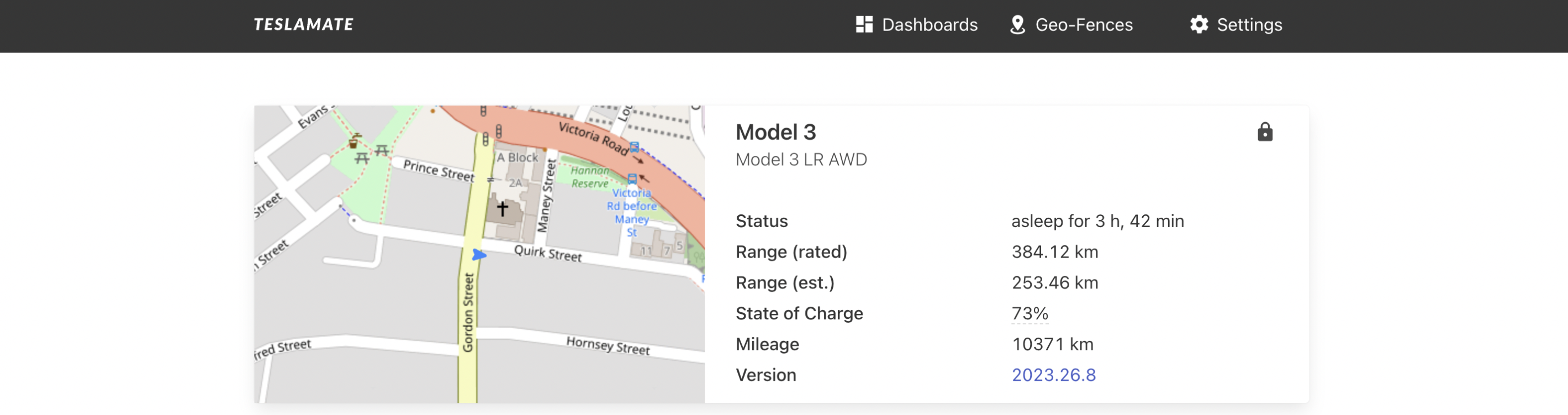
This result is scary , because the attacker does not even need to do authentication to login, they will be get hold of live location , data of the car.Lets see what else the attacker can do.
1.Edit Geofences data-
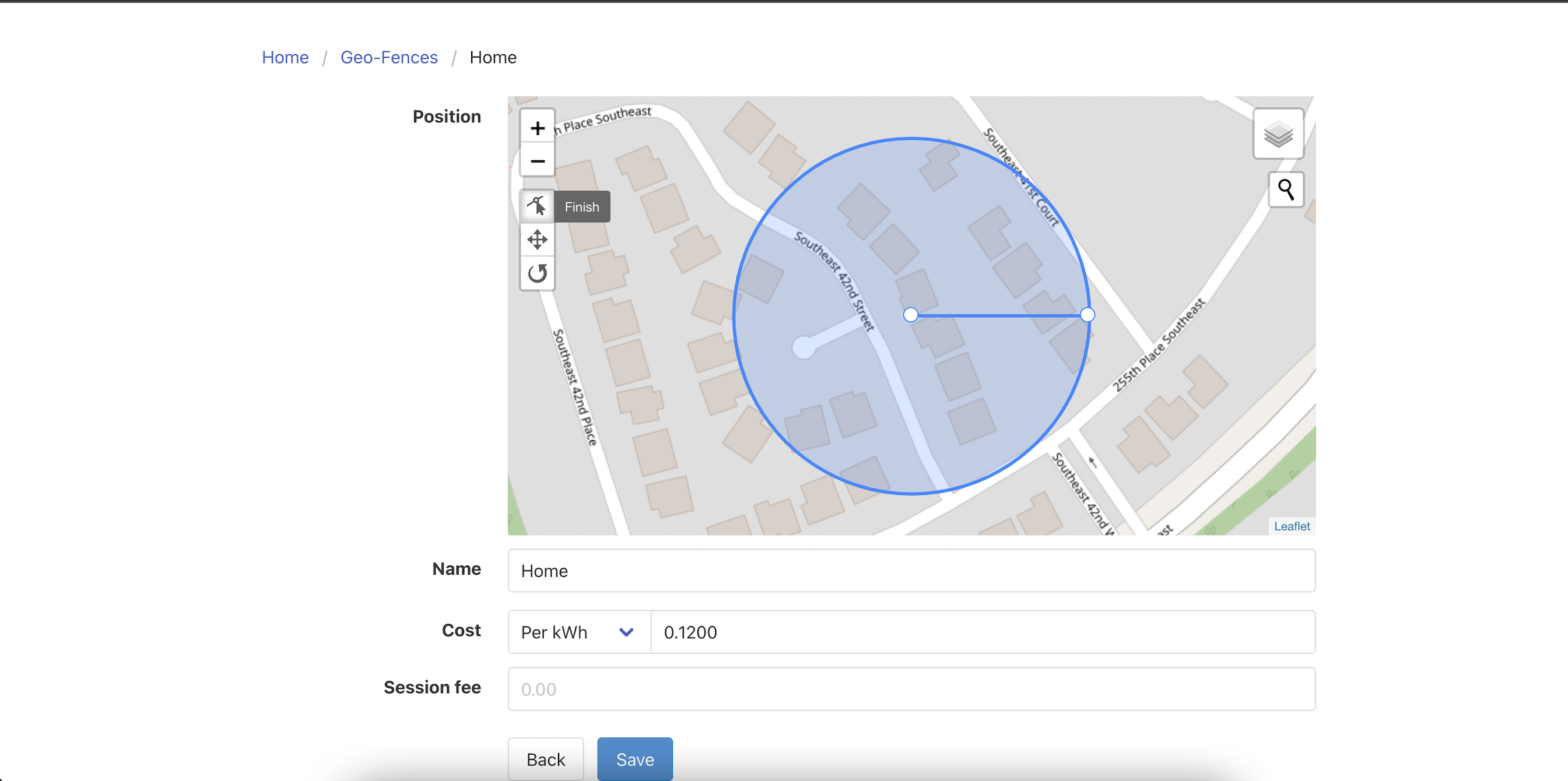
2.Make an Online car goto sleep-

3.Able to check whether the car is locked, if the doors are open, or if the driver is present
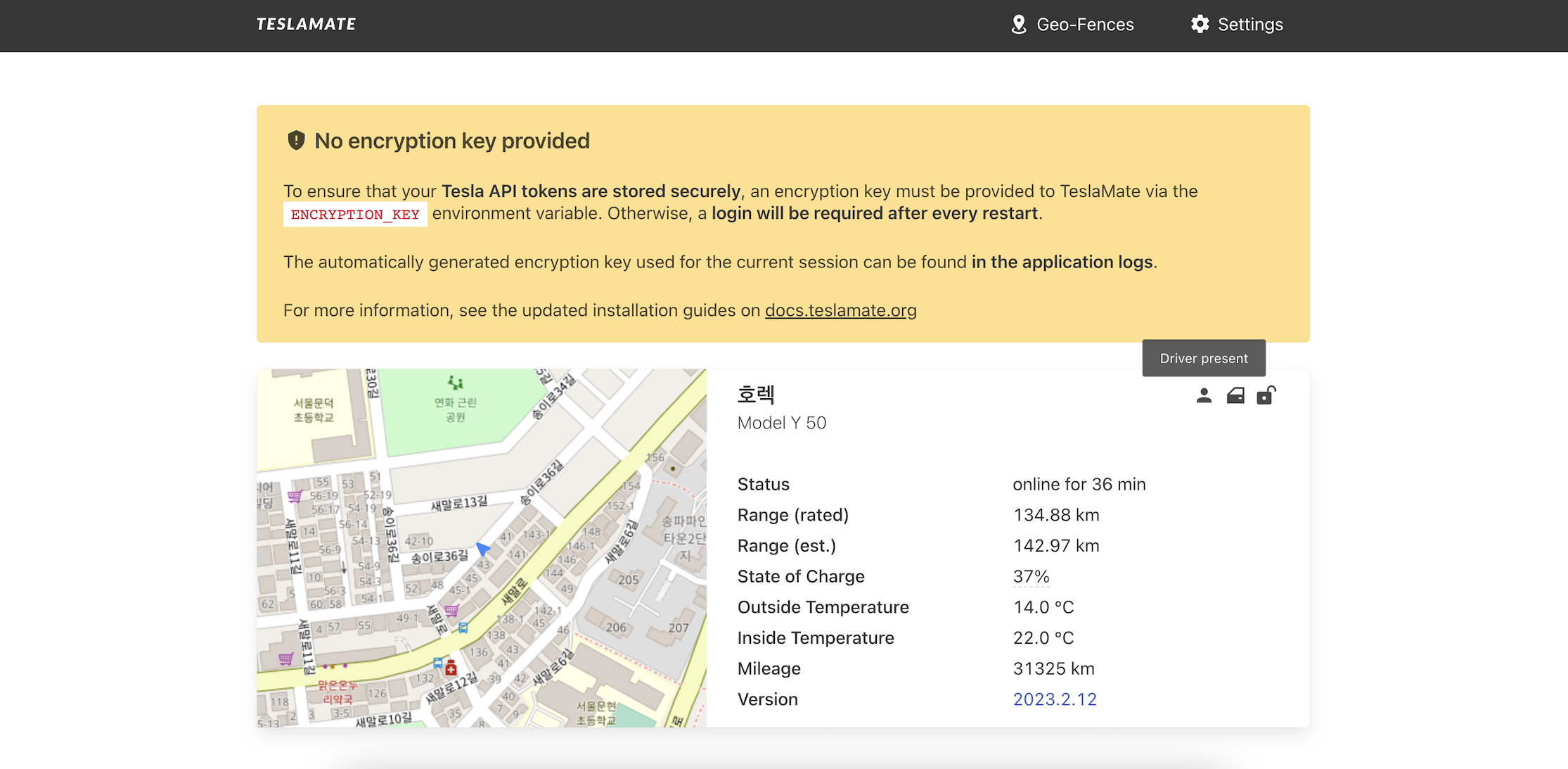


4.The most dangerous thing an attacker can do is, to track the live driving car
Impact:
If a user misconfigures third-party software, allowing unauthorized access to Tesla car data, it could have serious consequences for Tesla car owners.
Firstly, it could lead to a breach of privacy. The unintentional exposure of one’s live location without consent is a significant invasion of privacy, opening the door to potential misuse such as stalking or theft.
Secondly, misconfiguring geofences could inadvertently enable unauthorized access to sensitive information. Hackers could set virtual boundaries around the car and receive alerts, potentially compromising the owner’s daily routine and posing risks like planned robberies or other malicious activities.
Thirdly, the unintentional sharing of the car’s speed data might raise safety concerns. This could lead to misconceptions about reckless driving or create unwarranted worries for the owner.
Overall, the impact of misconfiguration-related vulnerabilities could be significant and potentially put Tesla car owners at risk. It underscores the importance of correctly configuring and securing third-party applications to protect personal data and maintain user privacy.


