“A white-label product is a product or service produced by one company (the producer) that other companies (the marketers) rebrand to make it appear as if they had made it. The name derives from the image of a white label on the packaging that can be filled in with the marketer’s trade dress. White label products are sold by retailers with their own trademark but the products themselves are manufactured by a third party.” – Wikipedia
IoT industry is one of the largest markets consisting of white labeled products and inside this IP / Surveillance IoT devices are leaders when it comes to white labeled products.
Security risks posed by such white labelling of IoT devices are very high.
Surveillance Systems
A conventional security analysis will never highlight the risks posed by the real underlying OEM and yet again let the organization live in a false sense of security unless the closest matching OEM test cases are also executed onto the IoT device.
Lets take a look into some broad examples of how underlying OEMs are detected. There are thousands of embedded smart devices indexed by search engines like Shodan and Censys. We found a few for our research purpose and analyse this a little further.
Below image shows how a single CP-Plus NVR (a IP Camera video storage hardware) also has reflected Dahua as its brand in TCP discovery port 2500

If for a moment even if we consider the above to be coincidental, the greater confidence about both devices being Dahua was now higher when we looked at the javascript file called “cap.js” present in the source code and the results that it showed.
CP PLUS Source

Output of cap.js file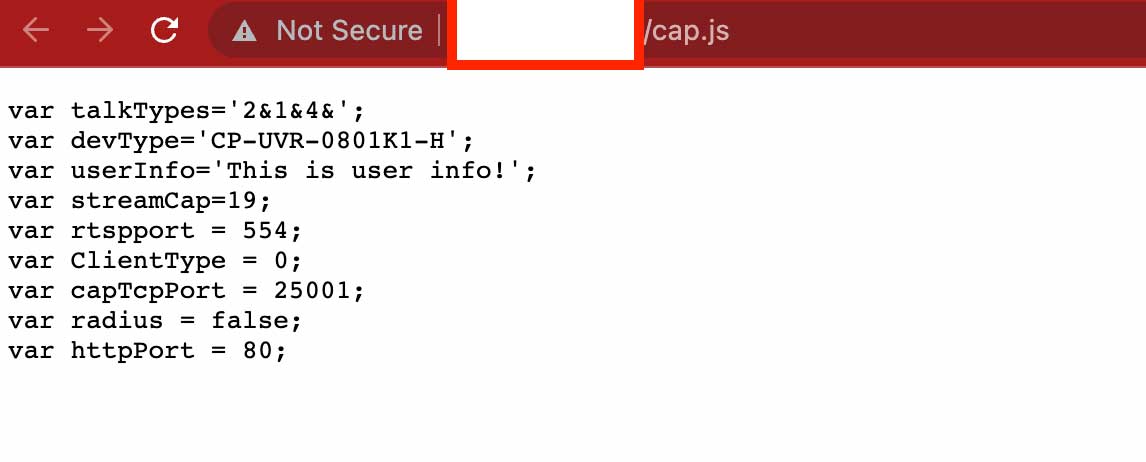
Dahua Source

Output of cap.js file
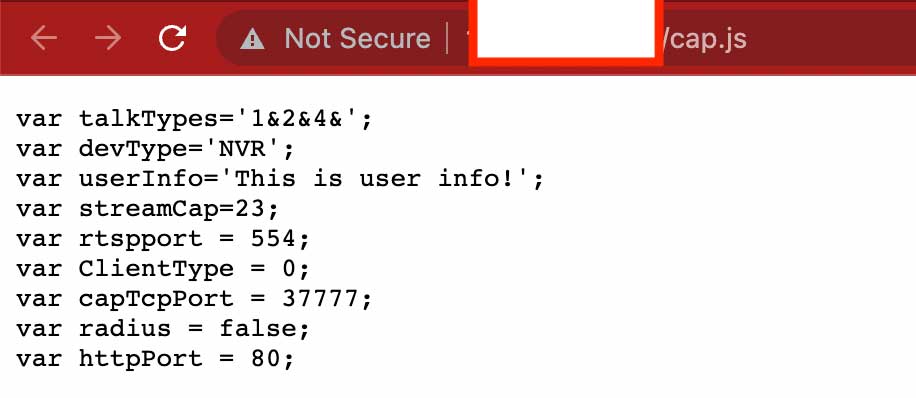
The results are identical along with the fields/metadata brought by the cap.js file. We did significant analysis on various such smart devices to identify patterns of similarity in source code, visual elements, web service calls, protocol responses to narrow down that the similarity score of between two IoT device.
EV Charging Stations
We expand our research to EV charging stations. EV is an emerging market and there are case studies on EVCS hacking incidents in the past. We will analyze the white-labelling phenomenon in EV world as well.
Here is a comparison of the login screens and source code of two well known EVCS players – GARO and ENSTO. Their similarity score is very high indicating the possibility of same firmware being used in both the devices.


Solving the Real OEM problem with Redinent
The prerequisite for any successful security assessment exercise is to effectively determine the correct underlying OEM so that the right set of test cases and vulnerabilities are identified. False identification of OEM leads to limited test coverage and leaves the IoT endpoint with undetected risks.
The Redinent Platform uses proprietary mechanisms through which it can determine the underlying similarity scores in OEM IoT/IIoT devices and then run the applicable test cases on that endpoint which leads to more accurate coverage and addresses the false sense of security problem. To learn more contact us at info-at-redinent.com.


